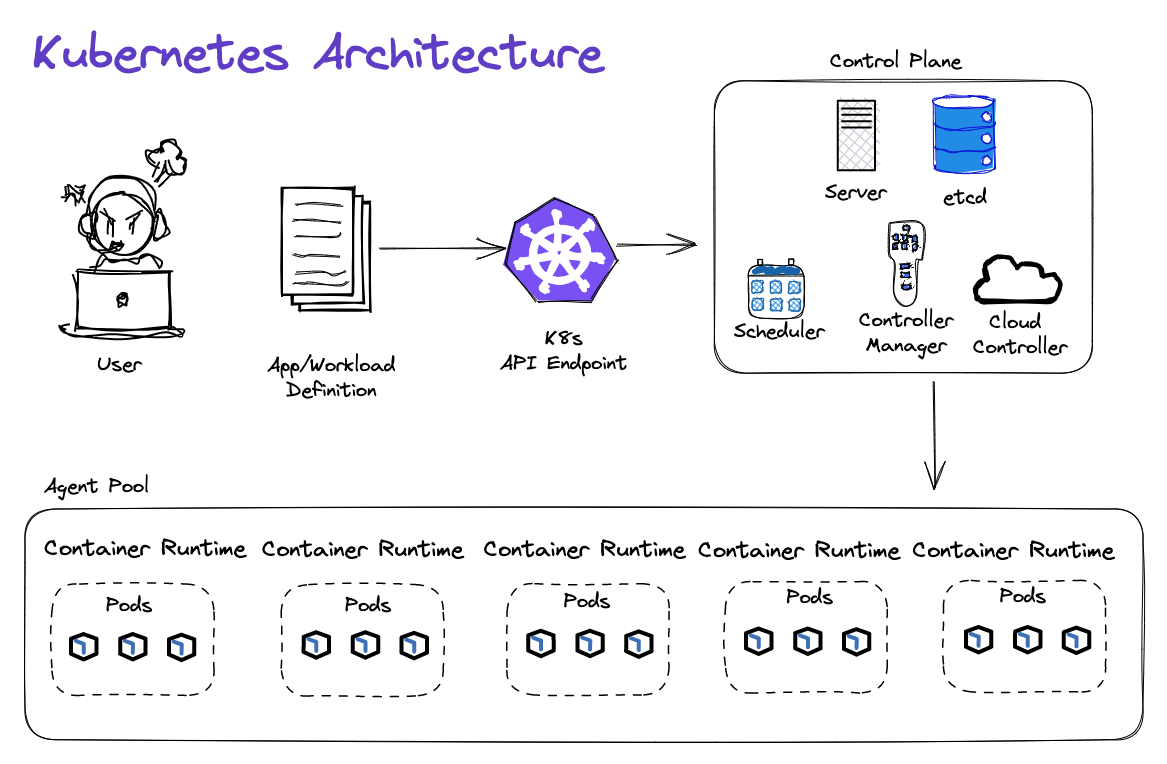
Kubernetes Architecture
Amazon Elastic Kubernetes Service (Amazon EKS) is a managed Kubernetes service to run Kubernetes in the AWS cloud and on-premises data centers. In the cloud, Amazon EKS automatically manages the availability and scalability of the Kubernetes control plane nodes responsible for scheduling containers, managing application availability, storing cluster data, and other key tasks.
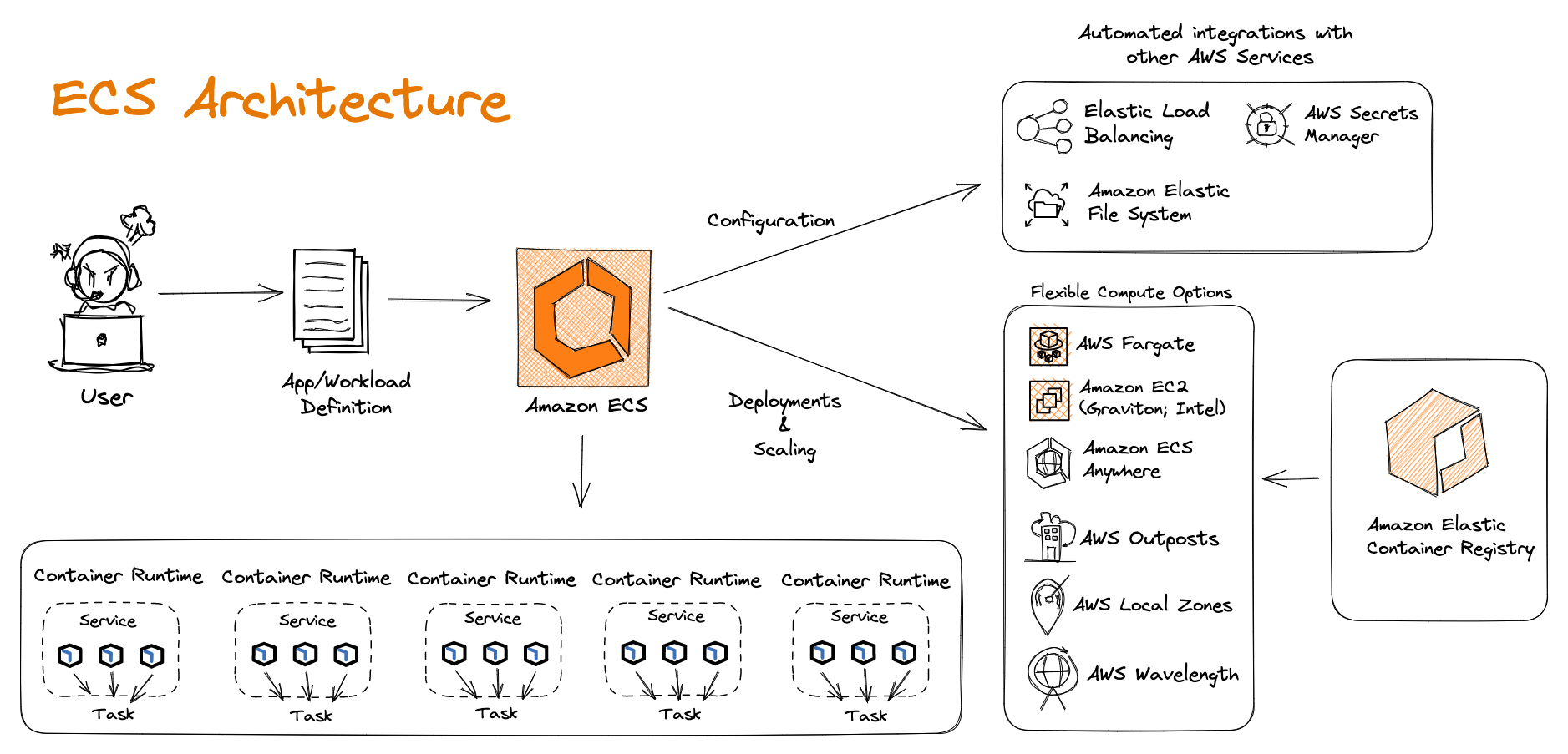
Amazon ECS Architecture
Amazon Elastic Container Service (Amazon ECS) is a fully managed container orchestration service that simplifies your deployment, management, and scaling of containerized applications. Simply describe your application and the resources required, and Amazon ECS will launch, monitor, and scale your application across flexible compute options with automatic integrations to other supporting AWS services that your application needs.
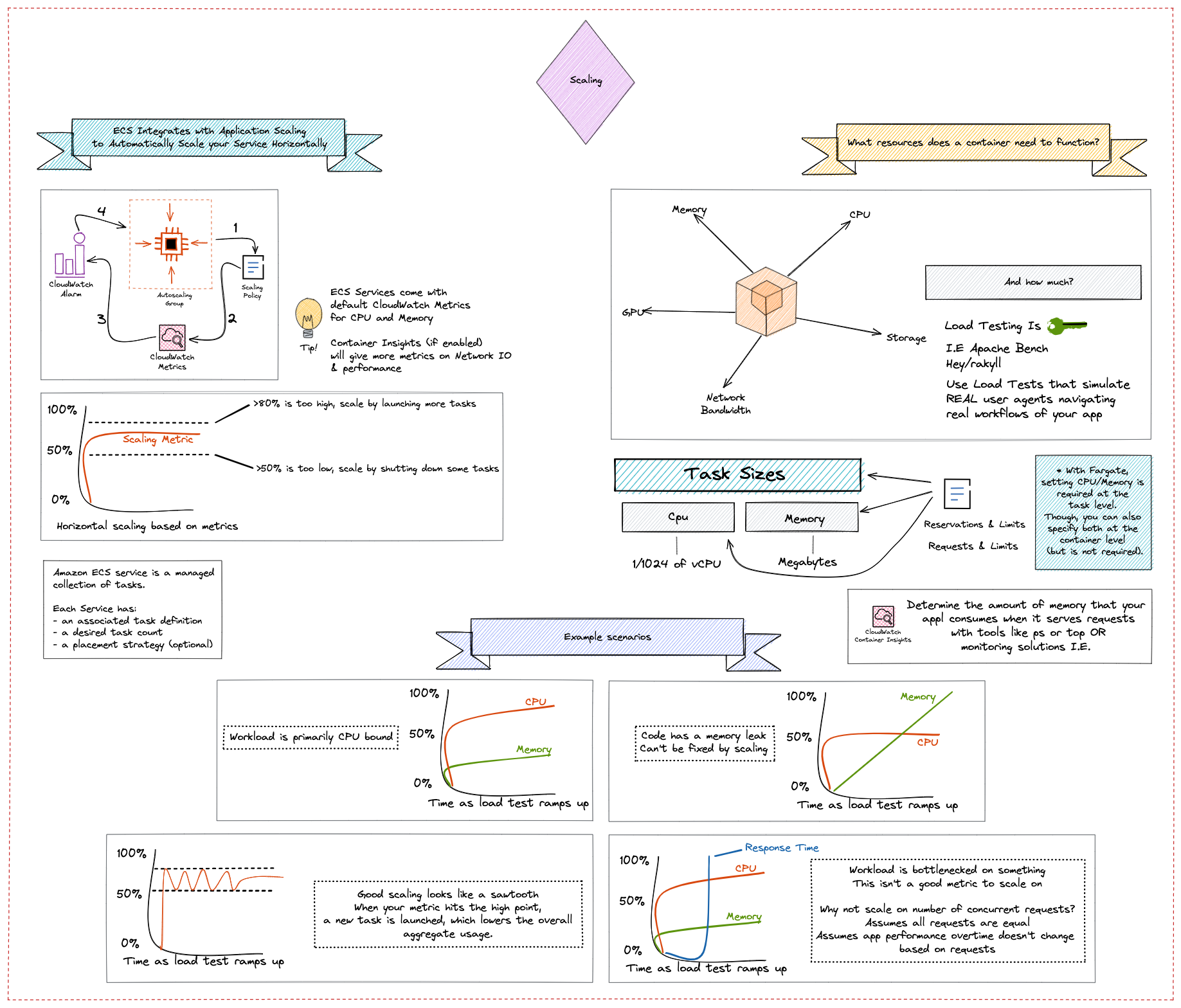
Container Platform Best Practices: Scaling
Amazon ECS is used to run containerized application workloads of all sizes. This includes both the extremes of minimal testing environments and large production environments operating at a global scale.
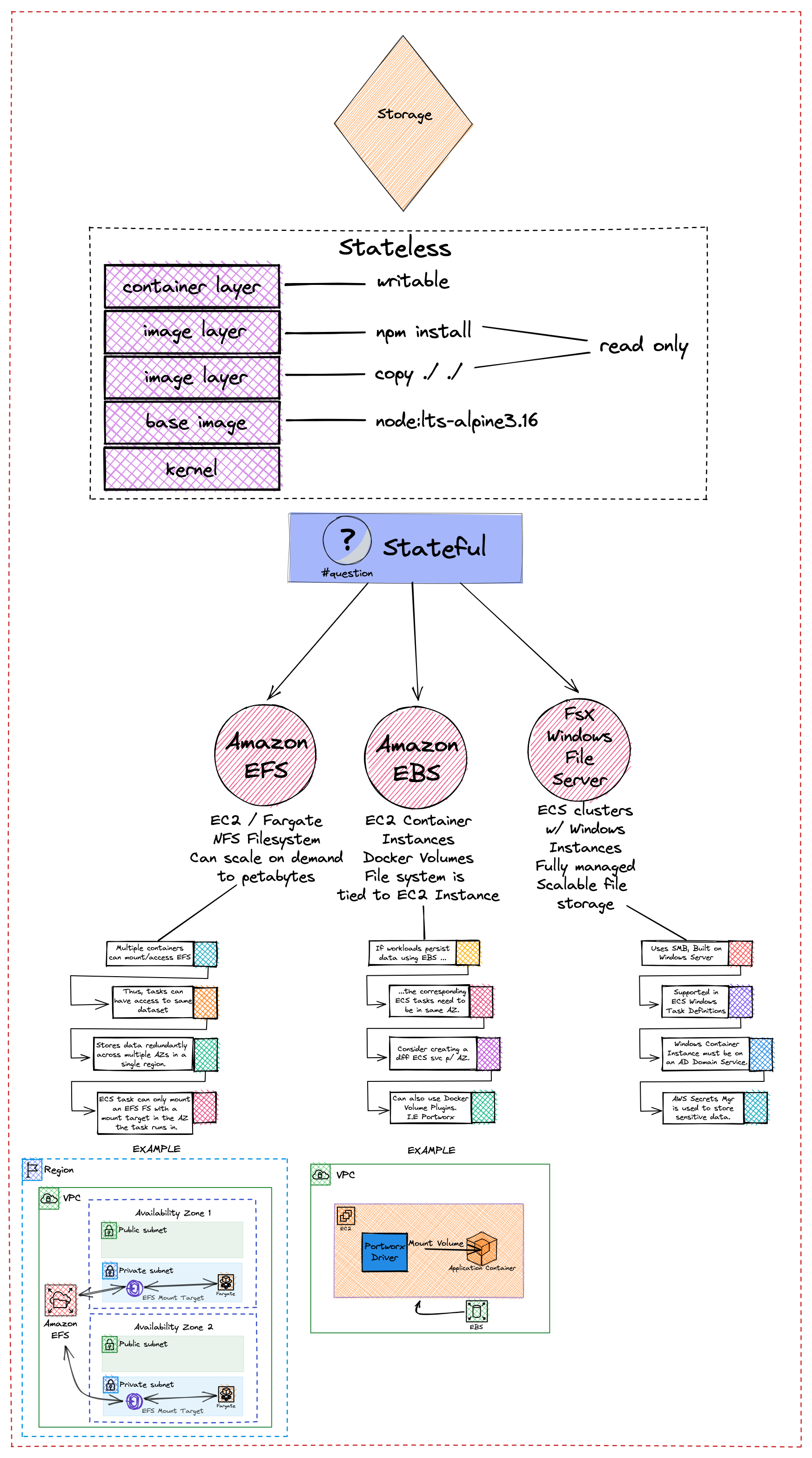
Container Platform Best Practices: Storage
You can use Amazon ECS to run stateful containerized applications at scale by using AWS storage services, such as Amazon EFS, Amazon EBS, or FSx for Windows File Server, that provide data persistence to inherently ephemeral containers.
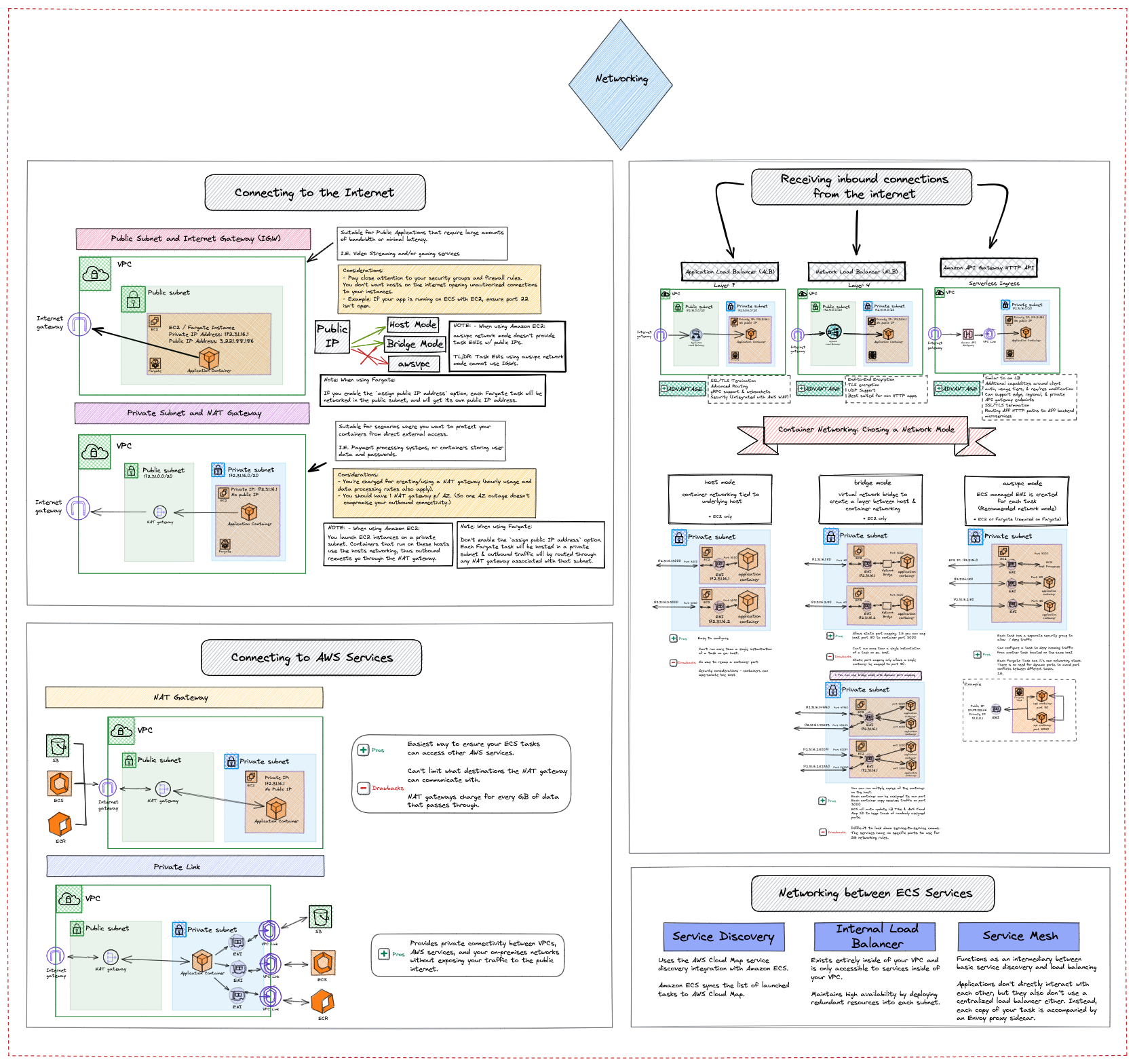
Container Platform Best Practices: Networking
This visualization presents the best practices for building a network where the components of your application can communicate with each other securely and in a scalable manner.
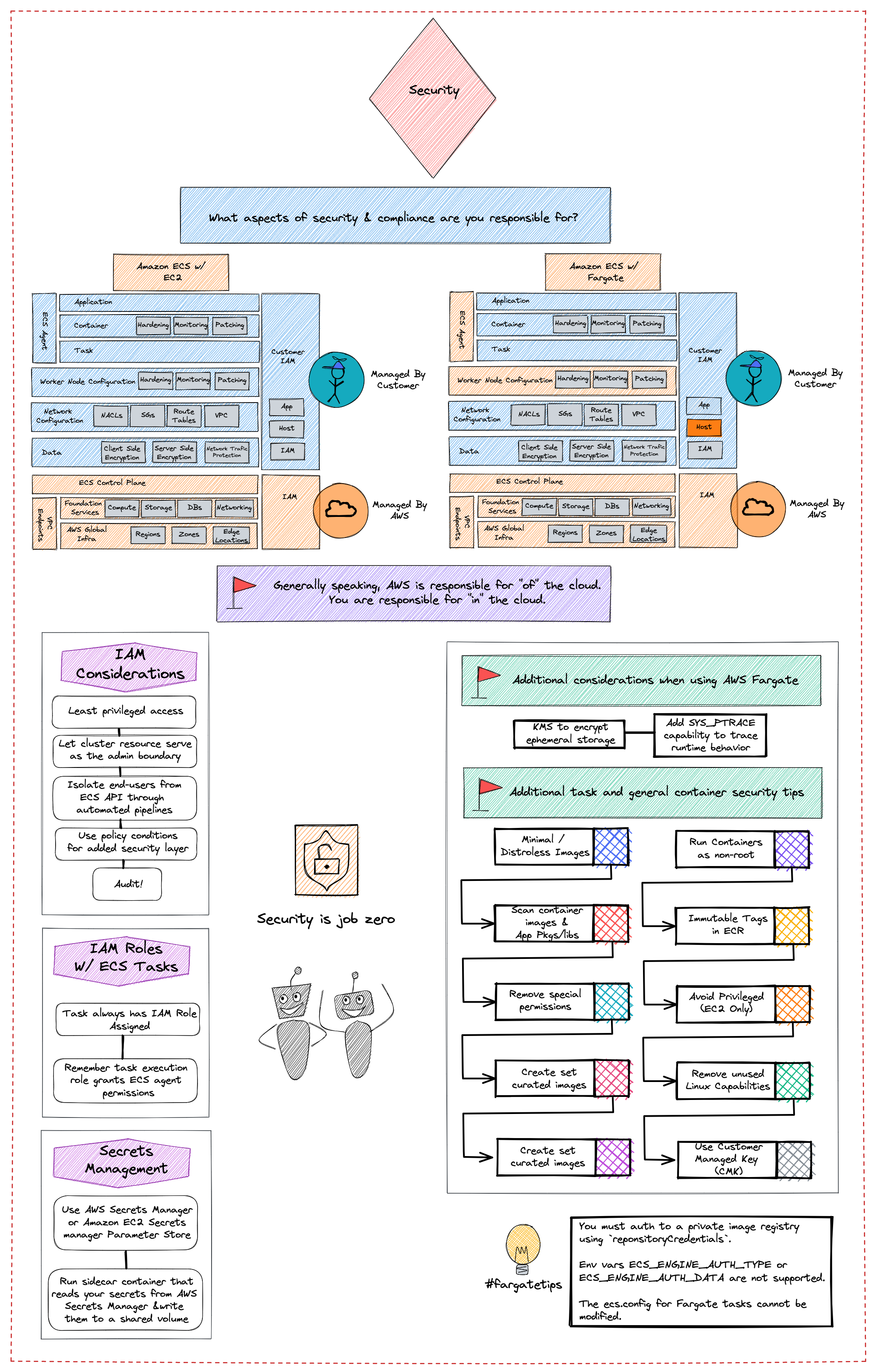
Container Platform Best Practices: Security
This visual provides security and compliance recommendations for protecting your information, systems, and other assets that are reliant on Amazon ECS. It also introduces some risk assessments and mitigation strategies that you can use to have a better grip on the security controls that are built for Amazon ECS clusters and the workloads that they support.