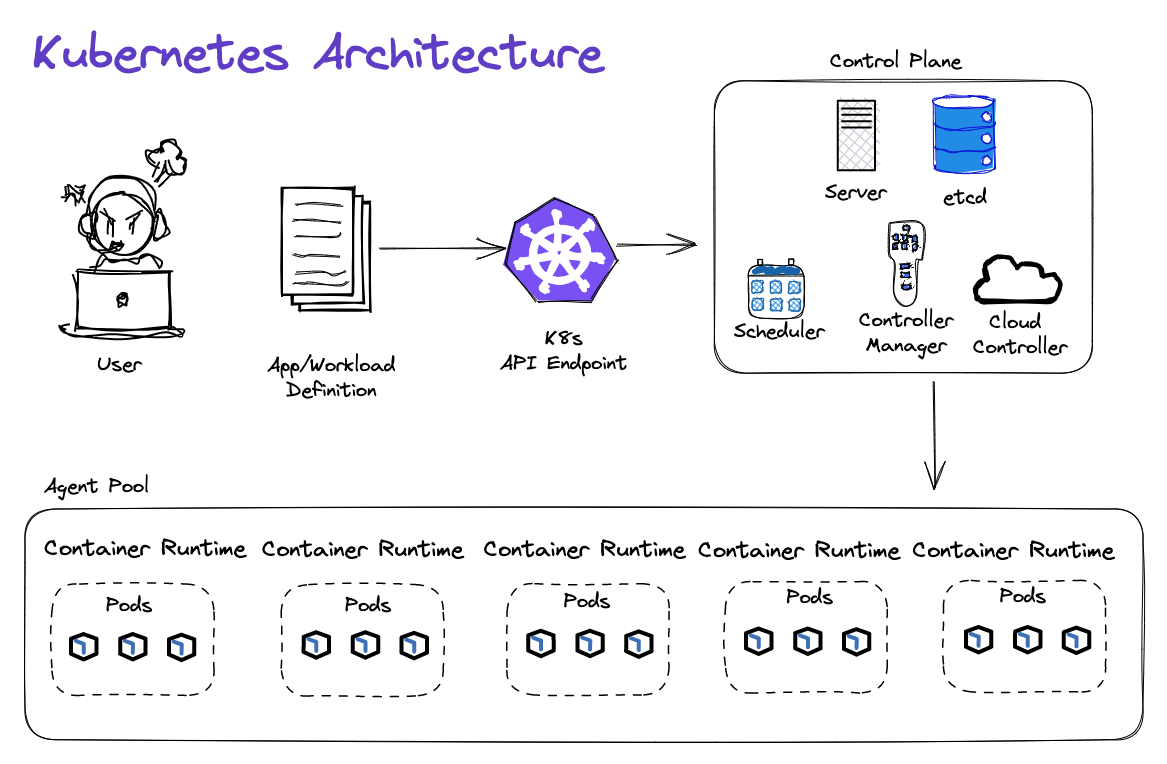
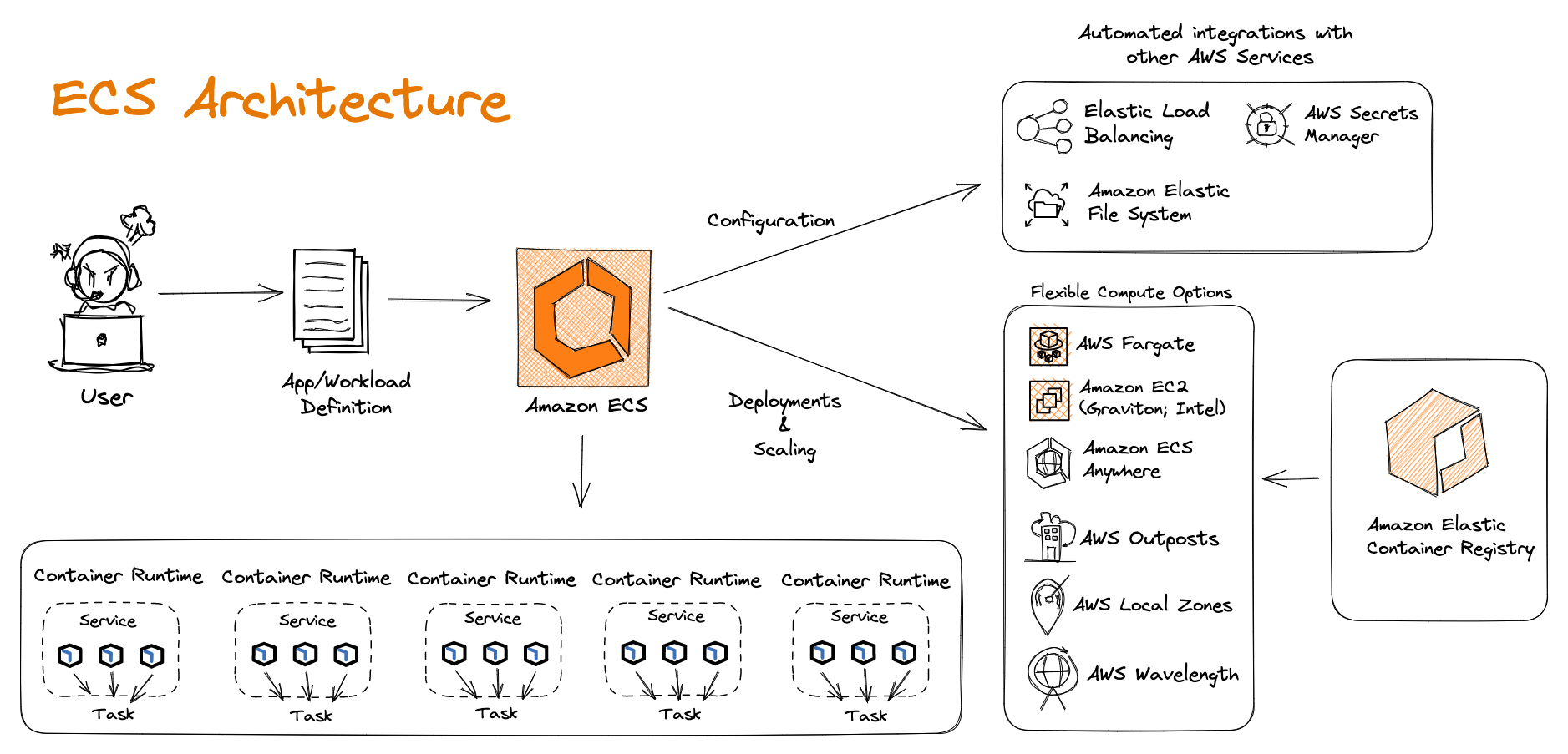
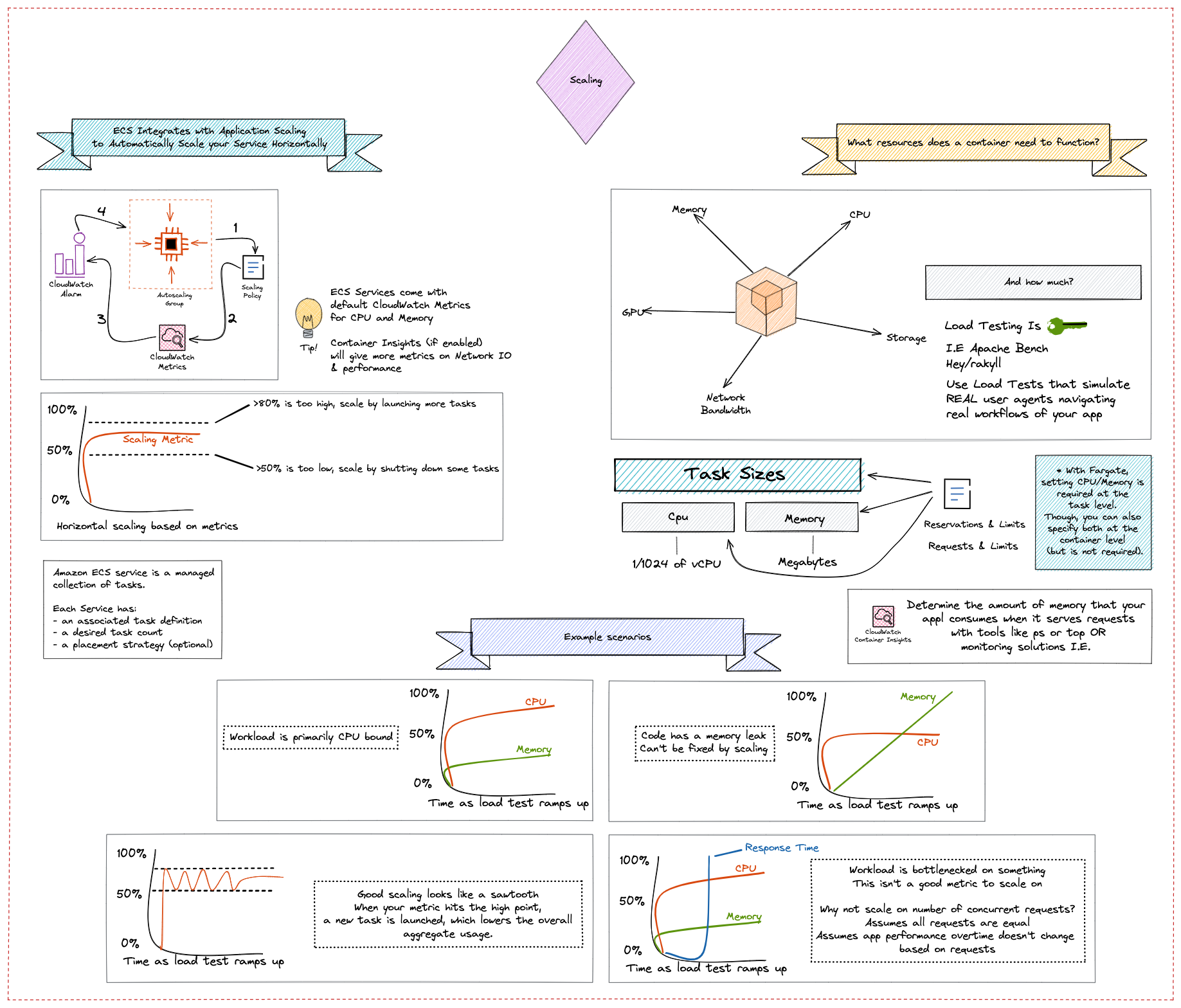
Container Platform Best Practices: Security
by Jessica Deen
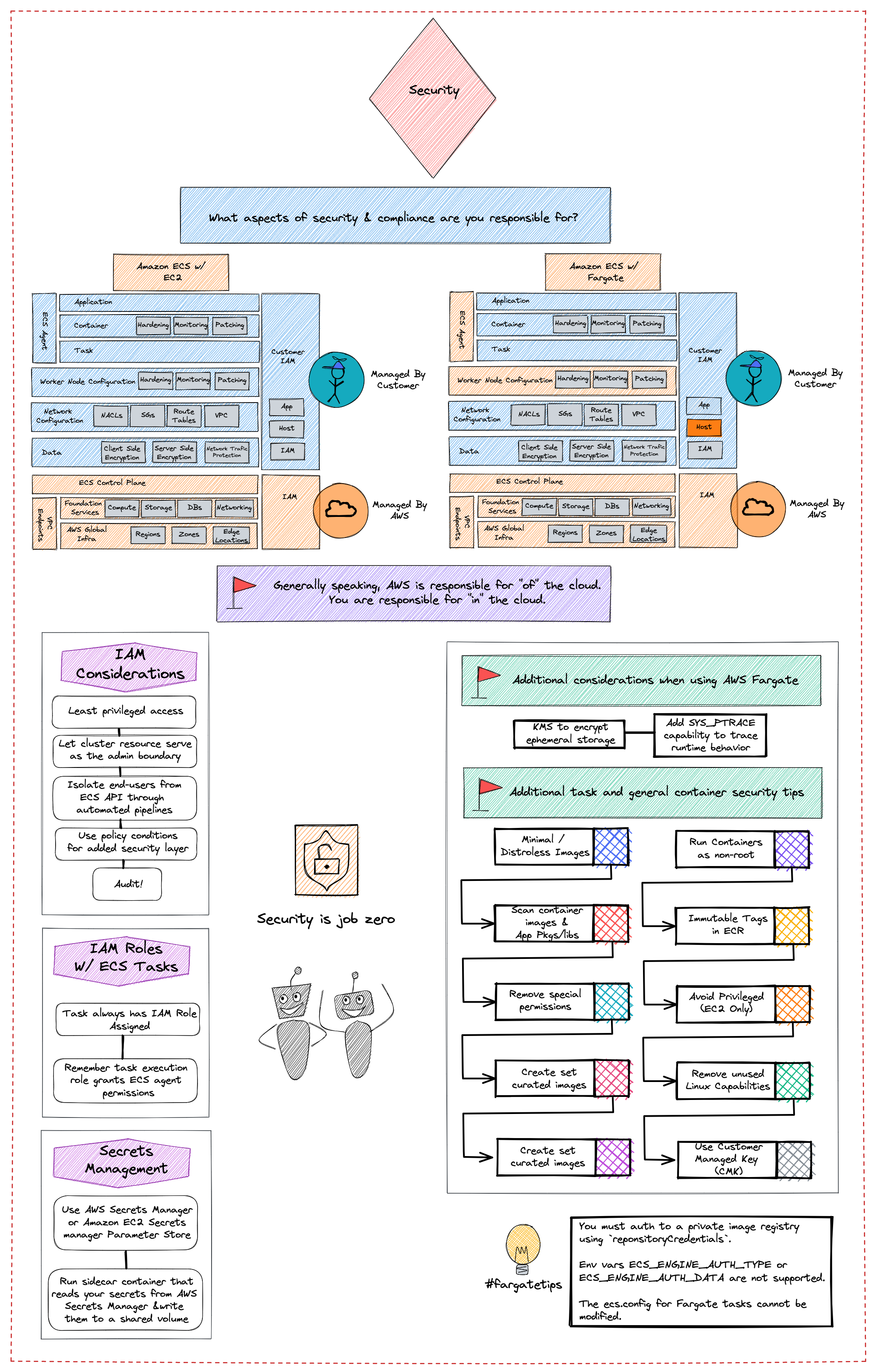
This visual provides security and compliance recommendations for protecting your information, systems, and other assets that are reliant on Amazon ECS. It also introduces some risk assessments and mitigation strategies that you can use to have a better grip on the security controls that are built for Amazon ECS clusters and the workloads that they support. Each topic in this guide starts with a brief overview, followed by a list of recommendations and best practices that you can use to secure your Amazon ECS clusters.